The HSOC Cyber Project Catalog
Real Work. Real Systems. Real Results. Every Fellow builds a career-ready portfolio across the four pillars of modern cybersecurity.
Defensive Operations
Focus: Detection, Analysis, and Incident Response.
SOC Alert Triage & Analysis: Investigate real-time alerts using SIEM tools (e.g., Splunk, Wazuh).
Deliverable: Formal Incident Response Report (IRR).
Threat Hunting & Forensics: Utilize packet analysis (Wireshark) to identify post-compromise activity.
Deliverable: Network Traffic Analysis Findings Report.
Mapped to CompTIA CySA+, ISC2 CISSP Domains.
Offensive Maneuvers
Focus: Vulnerability Identification and Ethical Hacking.
External Vulnerability Assessment: Scan and analyze client-facing infrastructure for weaknesses.
Deliverable: Comprehensive Vulnerability Assessment Report (VAR).
Web App Penetration Test: Identify and exploit common web vulnerabilities (OWASP Top 10) in controlled environments.
Deliverable: Penetration Test Findings and Remediation Plan.
Mapped to EC-Council CEH, CompTIA PenTest+.
Governance & Compliance
Focus: Policy, Risk Management, and Security Frameworks.
Risk Management Framework (RMF) Documentation: Map controls to a system and document security posture.
Deliverable: System Security Plan (SSP) and ATO Support Artifacts.
GRC Policy Development: Draft and refine organizational security policies (e.g., Acceptable Use, Data Classification).
Deliverable: Formal, Review-Ready Security Policy Document.
Mapped to ISACA CISM/CISA, ISC2 CISSP.
Special Programs & R&D
Focus: Emerging Technology and Customized Client Needs.
Cloud Security Audit: Perform a security review of a cloud environment (AWS/Azure) against best practices.
Deliverable: Cloud Security Posture Management Report.
Custom Tool Development: Design and script automation tools to assist in cyber operations (e.g., Python scripts).
Deliverable: Documented, tested, and functioning code repository.
Mapped to vendor-specific and advanced certifications.
Ready to Build Your Mission-Ready Portfolio?
START YOUR SKILLS-FIRST FELLOWSHIPAre you an organization looking to partner? Partner With Us.
The Skills-First Workflow: From Enrollment to Portfolio
Our projects are supported by a rigorous, professional process designed for success. Fellows don't just complete tasks; they follow a structured, job-aligned workflow that mimics a true corporate or government cybersecurity role.
1. Structured Onboarding & Preparation
Fellows begin with a guided profile creation and a comprehensive orientation. They complete necessary prerequisite training and familiarize themselves with our proprietary research and knowledge management tools before diving into client work.
2. Professional Project Management
Tasks are managed through a professional internal project management platform. Fellows receive assignments across 25+ cyber verticals, track their progress, collaborate with peers, and meet milestones under a simulated work environment.
3. Verifiable Portfolio Creation
The final step is the formal documentation of completed projects. This critical process ensures every deliverable—from incident reports to security policies—is verified and packaged into a job-ready portfolio that objectively demonstrates proficiency to employers.

Cyber Titans Virginia Internship Pilot Program

CTF Project: NOVA Hackathon

Cybersecurity Consulting: Future Kings Middle School Cyber Training

Cyber Escape Room Project: Future Kings
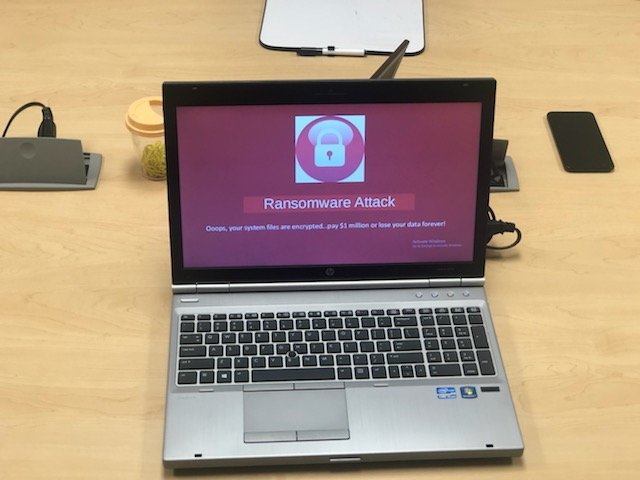
Cyber Escape Room Project: Future Kings
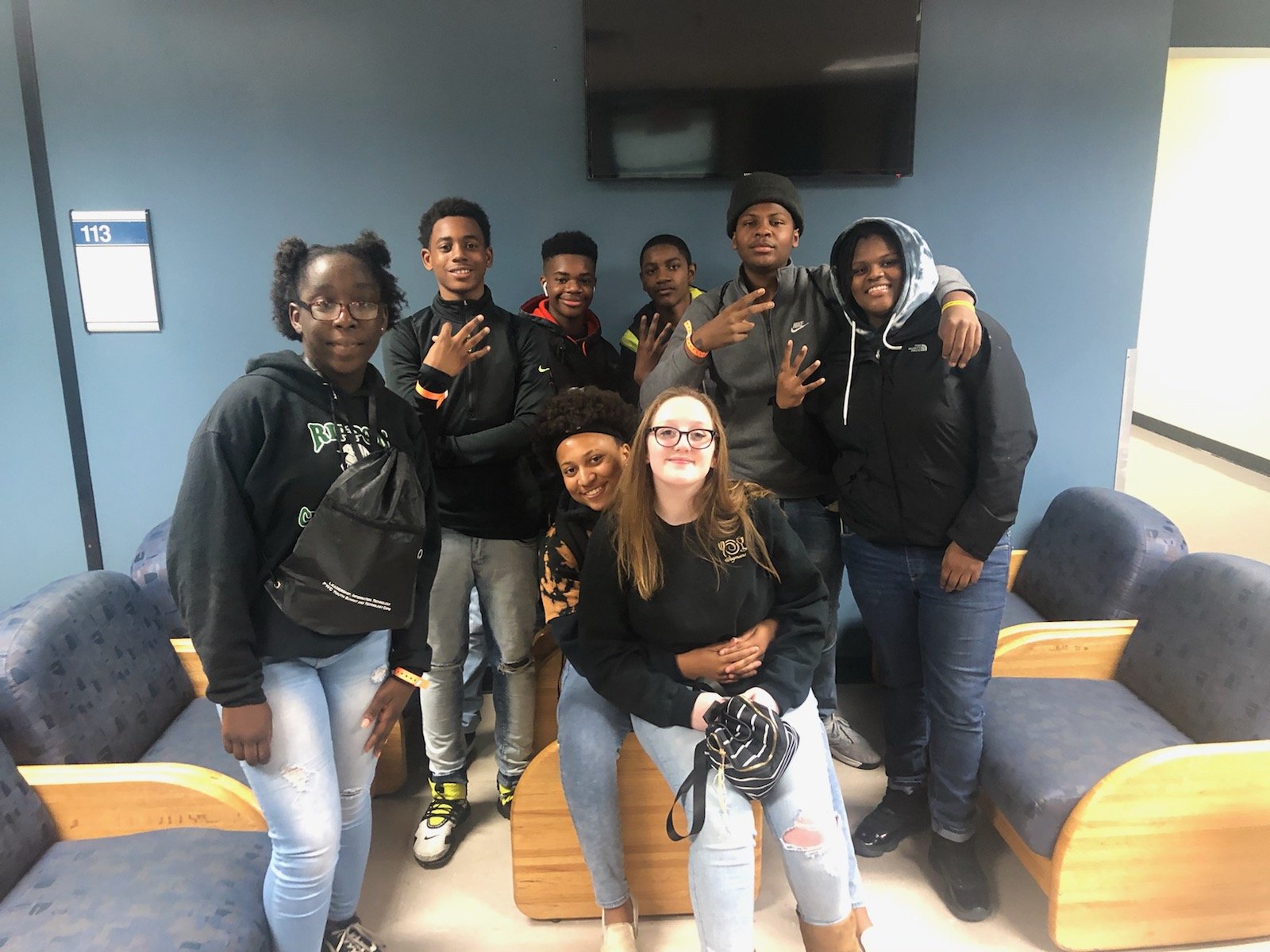
Cyber Escape Room Project: Winners

Cyber Escape Room Project: Debrief

CTF Project: NOVA Hackathon
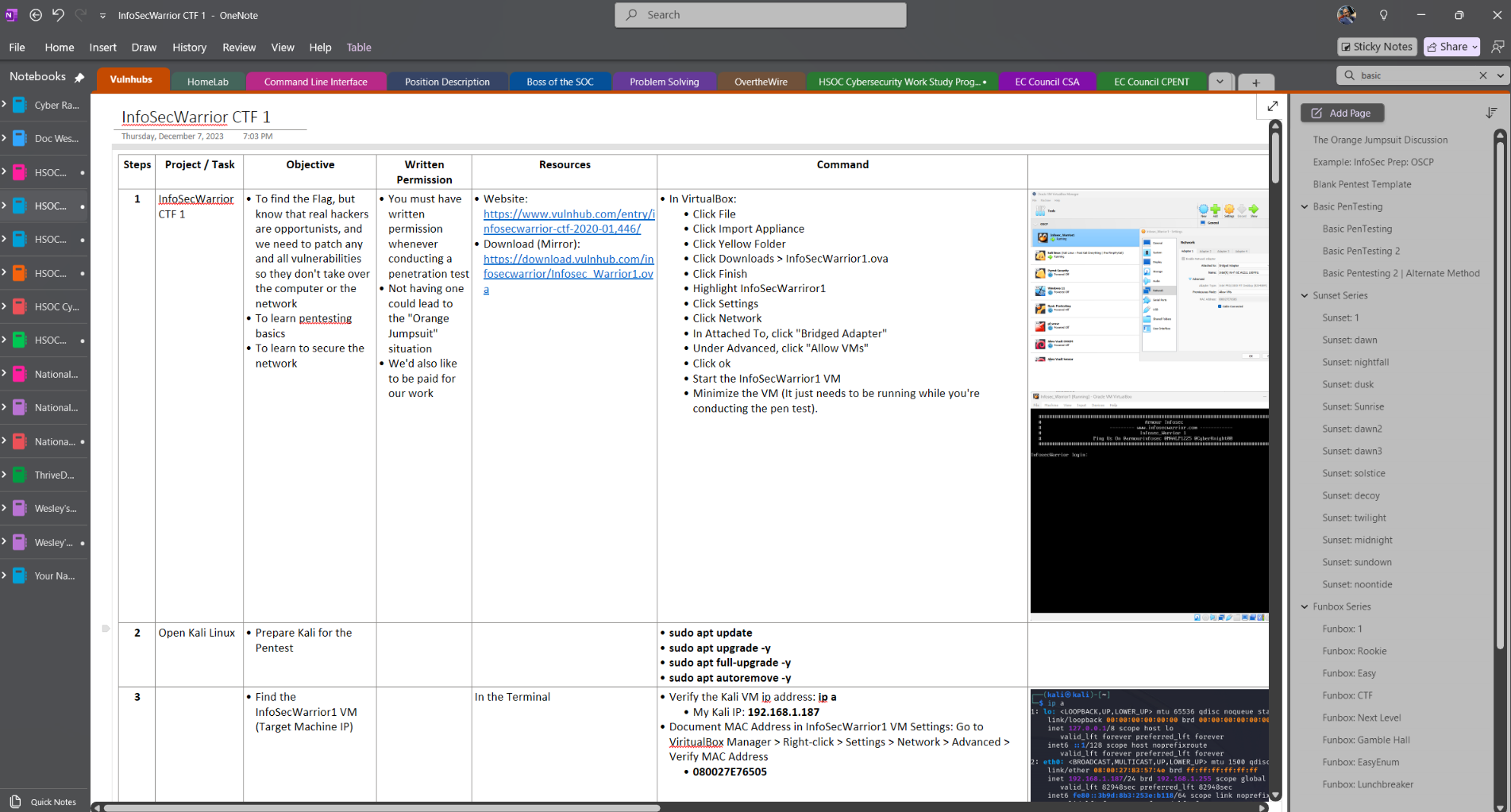
Pentesting Project: Report Writing
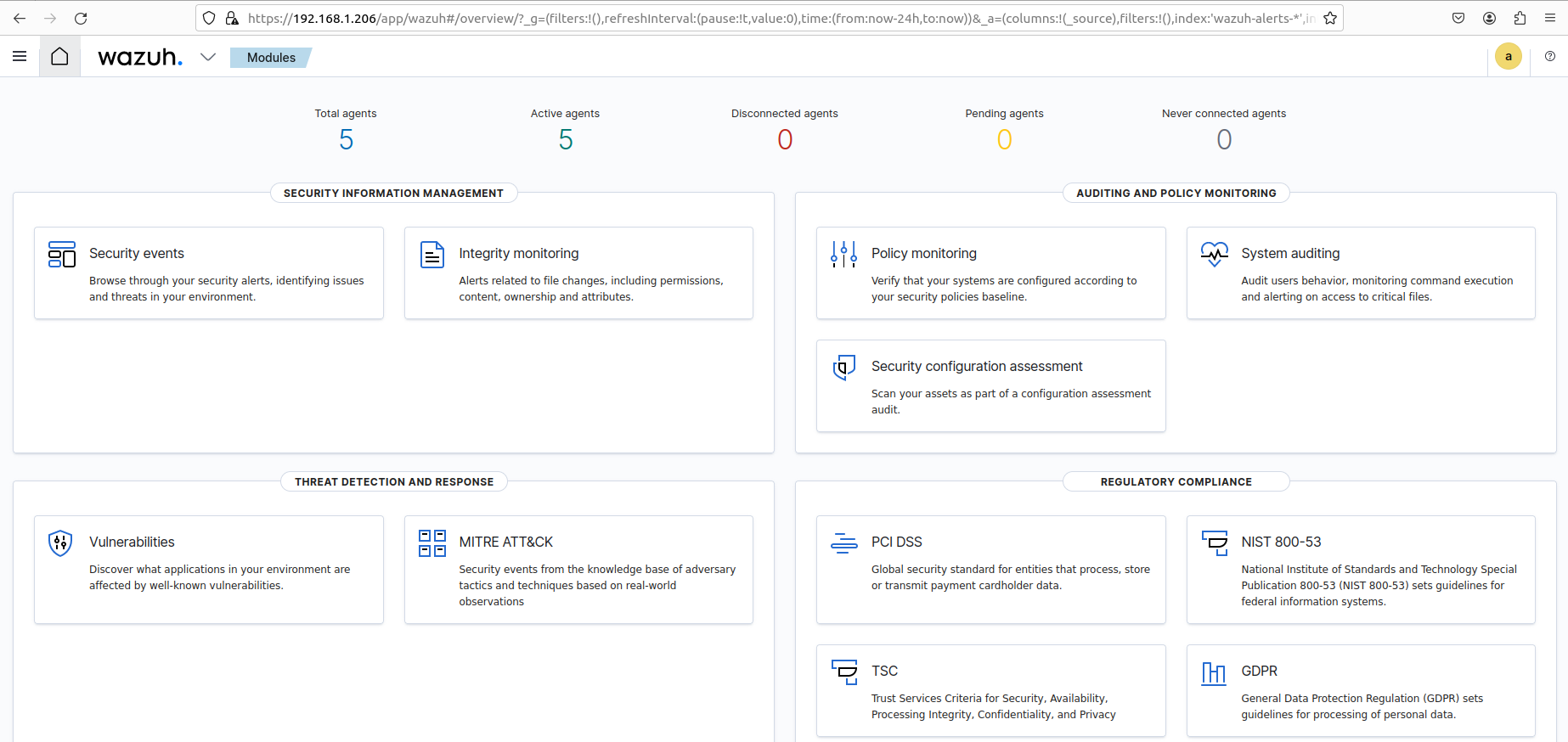
HSOC Project: Wazuh Installation
SOC Project: Splunk SOAR Rocky Linux Installation
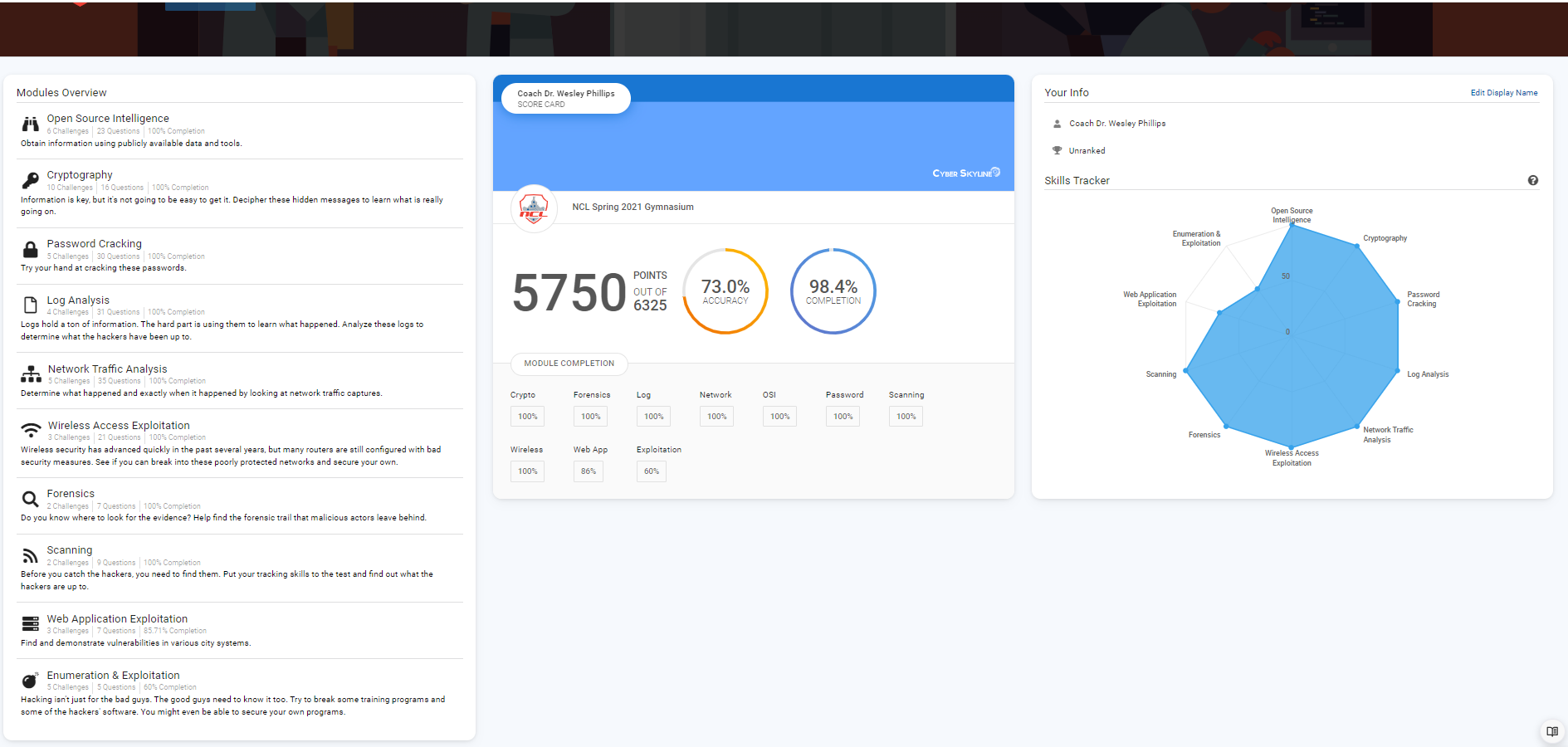
CTF Project: National Cyber League
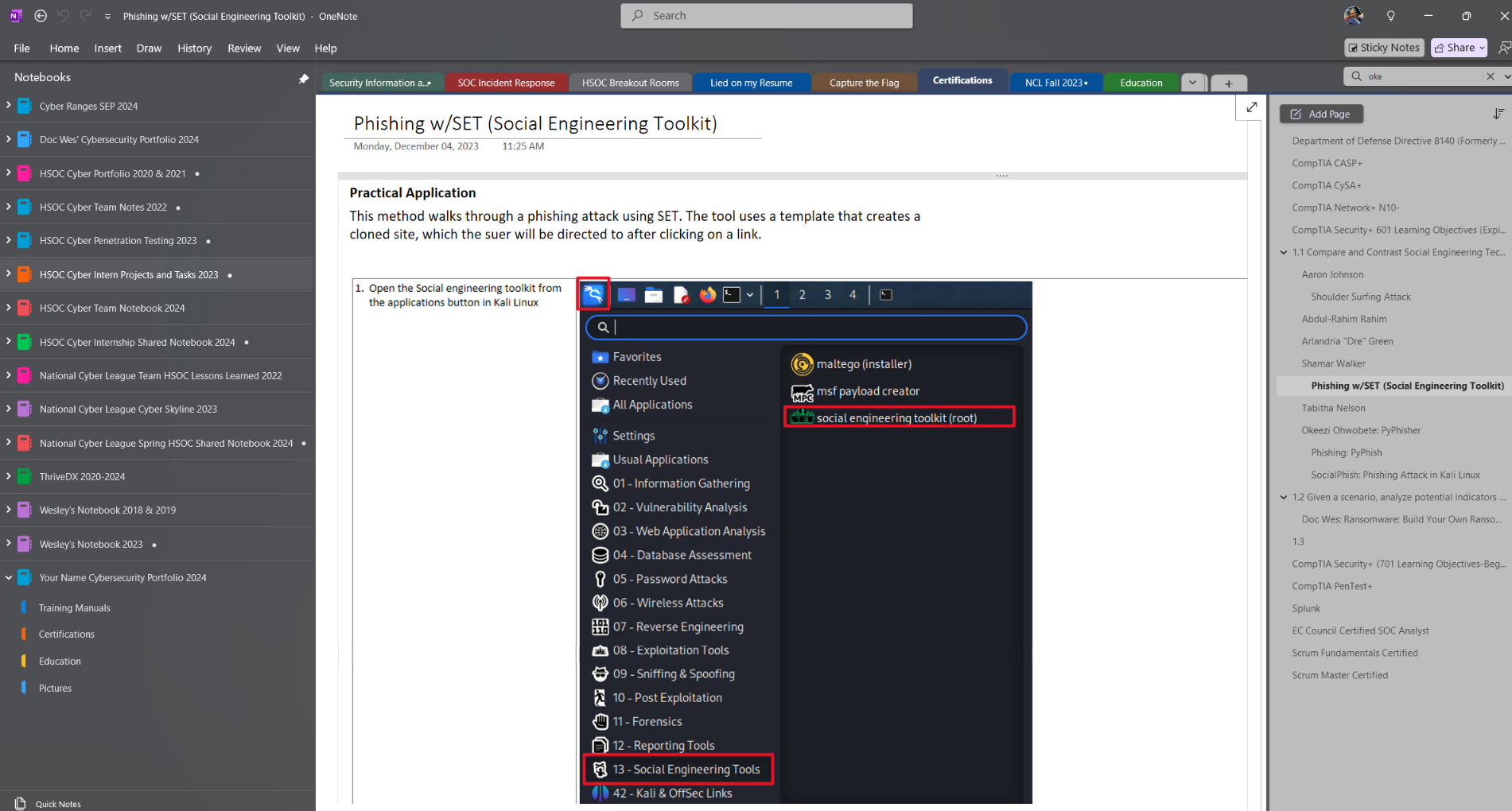
Pentesting Project PyPhisher Presentation and Discussion
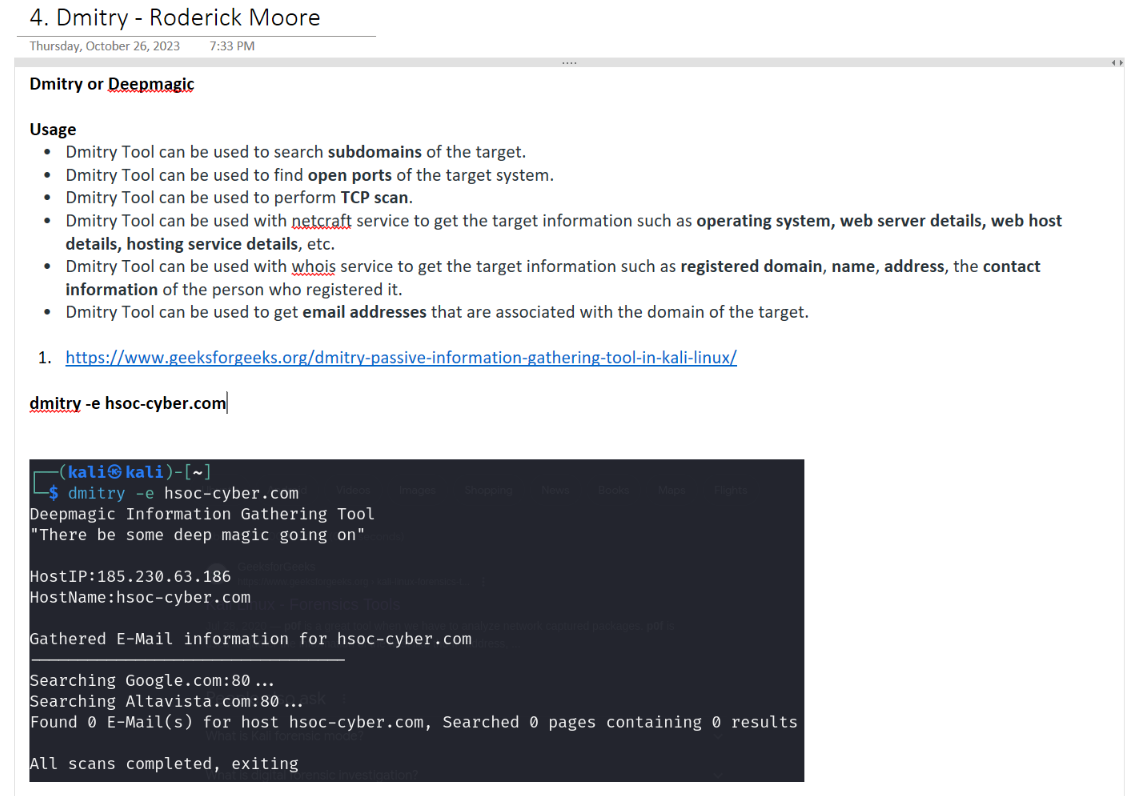
Secure Project Management Project: Research and Present Dmitry
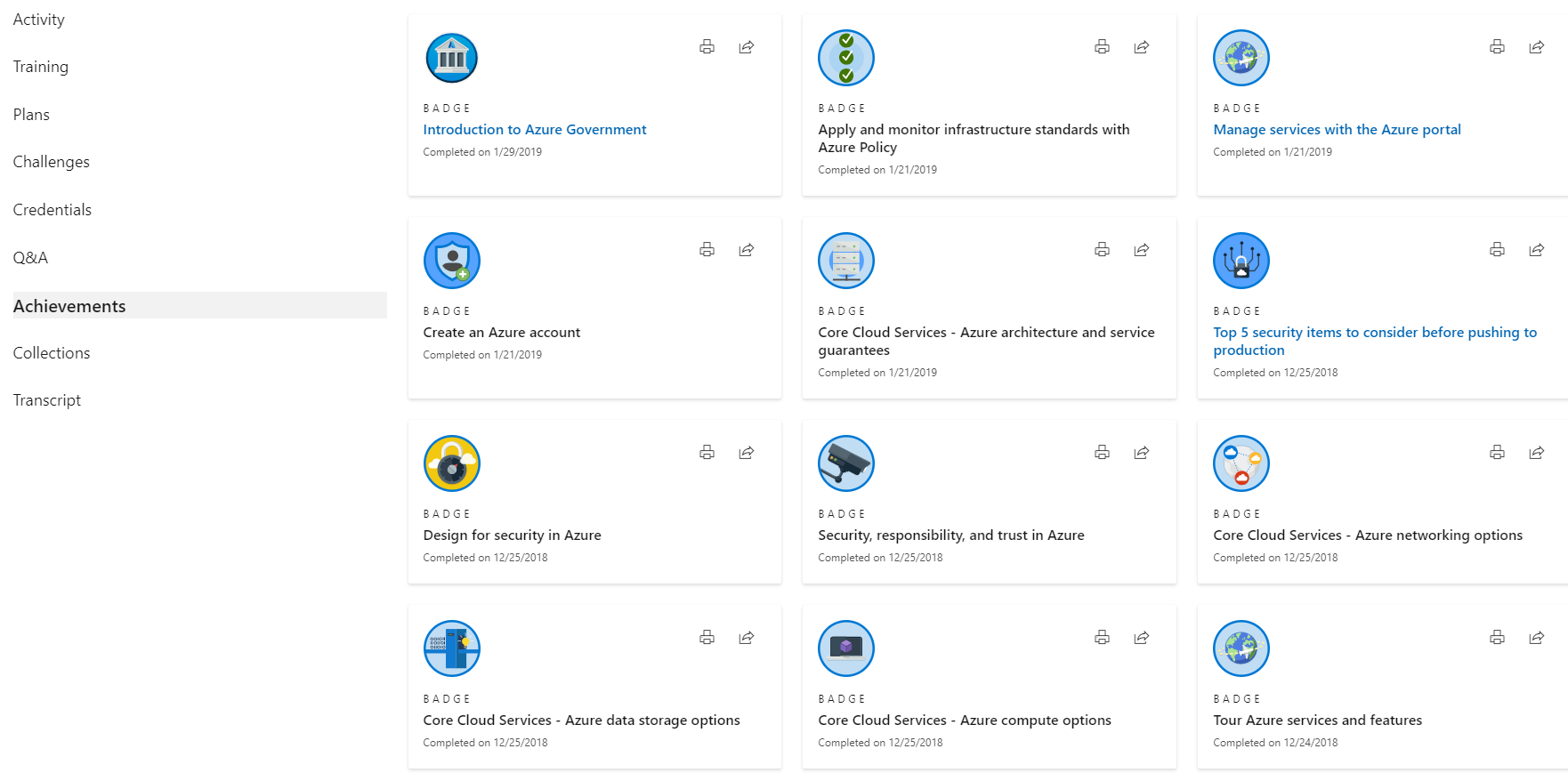
Cloud Security Projects: Learning Azure
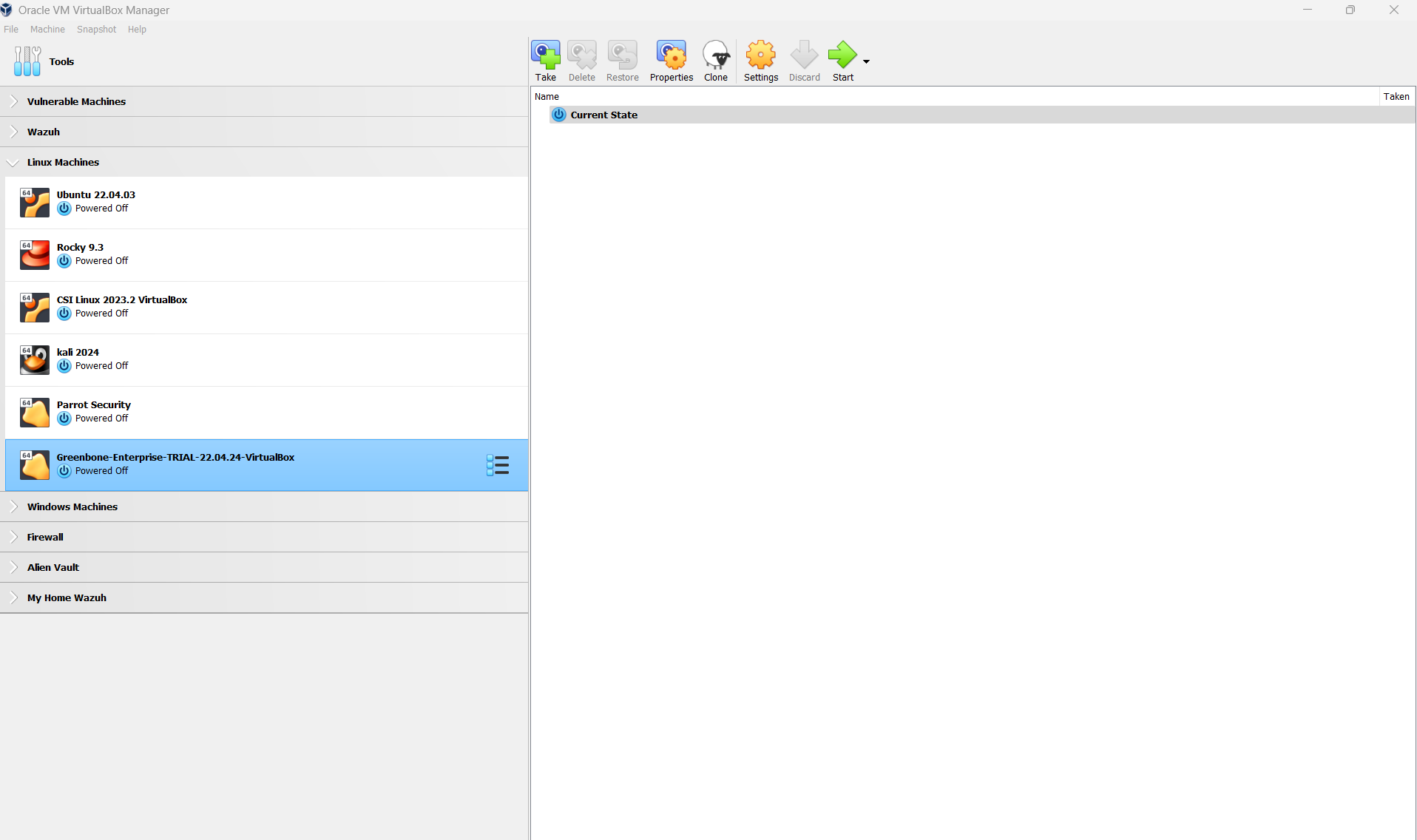
HSOC Project: Virtualbox Installation and Organizatioin
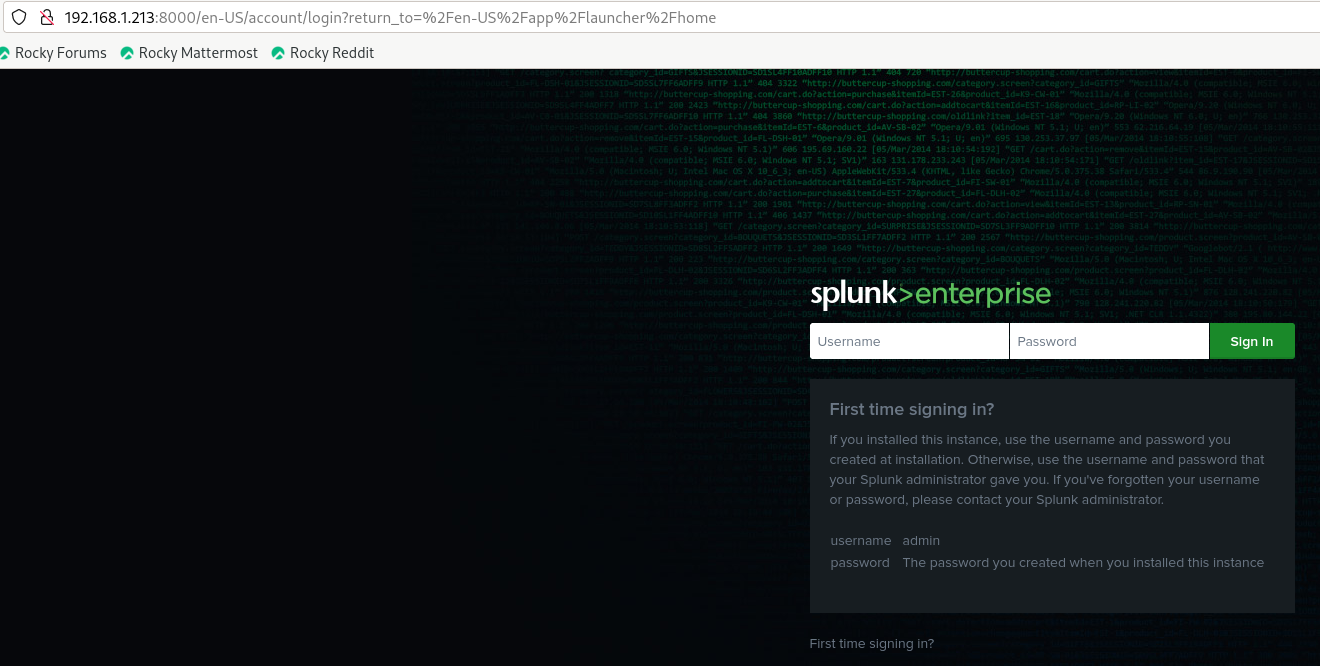
NOC Project: Splunk Enterprise Rocky Linux

HSOC Cyber Welcomes Belen and Maggie of the Cyber Titans Virginia Internship Program (Cyber Titans VIP)
